The vulnerability, which our friend Charlie at SemiAccurate has been trying to get the company to fix for nearly five years now, affects every Intel platform with AMT (Active Management Technology), ISM (Intel System Management) and SBT (Small Business Technology). The list includes every desktop and notebook platform Intel has released since first-generation Core series Nehalem processors in 2008 through the 7th-gen Kaby Lake processors currently on the market.
In Intel's May 1st security advisory, any machine installed with AMT (Intel vPro suite), ISM (Intel Servers) or SBT firmware versions 6.x through 11.6 can allow an attacker to “gain control of the manageability features provided by these products” either locally or remotely. On the local end, Intel says “an unprivileged network attacker could gain system privileges to provisioned manageability SKUs (Intel AMT and ISM)". At the remote end, an unprivileged attacker could can local system privileges on Intel AMT, ISM and SBT.
While most consumers do not have Intel’s management solutions provisioned or in use, sometimes they can be installed without people knowing. The easiest solution for this vulnerability is to simply “uninstall all the pieces”. For enterprise and business users, especially on Intel vPro systems, this is an exploitable security hole in the Intel Management Engine (ME) interface, not the CPU firmware. Even if a machine does have AMT, ISM or SBT provisioned, it is still classified as being locally vulnerable to attack but not remotely vulnerable.
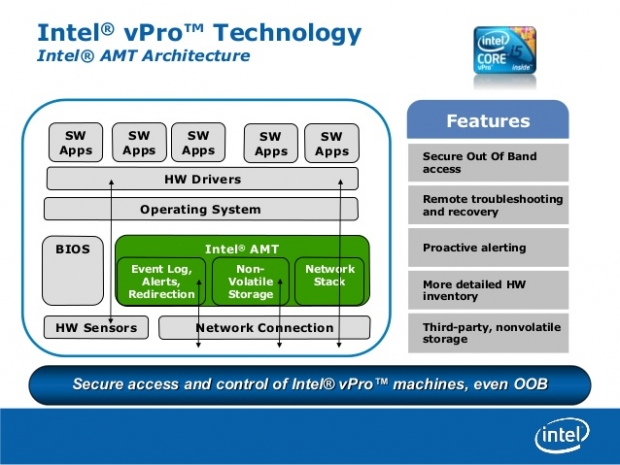
Intel AMT bug on Intel vPro systems: remote disk access and logging through privileged access
The vulnerable Active Management Technology (AMT) service is part of the Intel Management Engine, which is built into PCs with Intel vPro technology. Since the Intel ME interface controls hardware LAN ports it has direct memory access to the rest of the system. As such, it can read and write to any memory or storage address on the system, which includes bypassing drive encryption. SemiAccurate has done some investigation and suggests that the engine can even read and write to the display without any data logging involved, while being able to send data over the network at any given time. For corporate enterprises, this would seem to include re-imaging hundreds or thousands of systems without privileged access, regular remote disk checking and virus scanning, and logging millions of user commands inputted by keyboard with legitimate disk subsystem access.
Given the hundreds of millions of AMT, ISM and SBT capable systems that have been shipped worldwide over the past nine years, Intel’s latest escalation of privilege discovery easily affects almost as many people as the Heartbleed OpenSSL bug that left a permanent stain on the World Wide Web’s security layers in early 2014.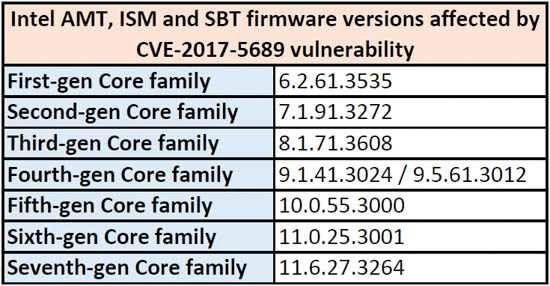
Intel has known about this for years
For any user not involved in the IT security field or up to date on routine security disclosures, any patch marked as “critical” tends to get downplayed over time as software vendors deploy so many of them without much differentiation. This softening of the human psyche often leaves the Level 5 “highly problematic” bugs to get discounted in the process. But when a security hole similar to Heartbleed has gone unpatched for almost a decade, there is a sign that Intel had reasons not to have it patched immediately due to some handshake agreement that we may never hear about.
Firmware updates on the way as Intel releases “Detection Guide”
Currently, the bug can be fully addressed with a firmware-level update. But given the varying level of ambition and response from system vendors, there is no saying how long it will take for Dell, HP, Acer, Asus, Lenovo and other mainstream manufacturers to issue these updates. For now, Intel’s CVE-2017-5689 page lists a few mitigations that users can try through the Intel SCS Discovery utility that runs in a command prompt window. Interested end-users and IT admins can use the company’s Detection Guide to check whether their system has an affected firmware version installed.