The bug, described as “unusual,” is capable of being exploited without the recipient even opening an infected email or instant message. Microsoft’s anti-malware product, Windows Defender, would simply need to scan the malicious content for the exploit to be triggered. On some Windows 8, 8.1, 10 and Windows Server machines, scans are set up to occur almost instantly using “real-time protection,” which gives users and admins very little time to react to the unforeseen product flaw.
High risk for machines with “real-time protection” enabled
In short, any system with the “real-time protection” feature turned on is going to be affected first, as the Malware Protection Engine inspects files as soon as they appear on the file system. The company says the vulnerability was severe enough to create and include a patch in its regular Patch Tuesday update rollout, which often occurs on the second Tuesday of each month.
The vulnerability was discovered by Google Project Zero cyber-security researchers Tavis Ormandy and Natalie Silvanovich on Saturday, who describe the issue as being related to the “NScript” component of MsMpEng.exe, a core process of Windows Defender that scans downloaded files for spyware and quarantines or removes them.
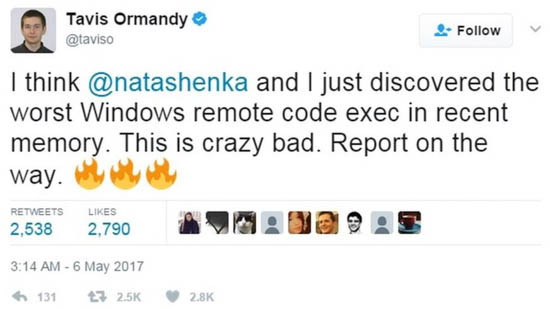
Source: Twitter
“NScript is the component of mpengine that evaluates any filesystem or network activity that looks like JavaScript,” Ormandy says on the Chromium bug report page. “To be clear, this is an unsandboxed and highly privileged JavaScript interpreter that is used to evaluate untrusted code, by default on all modern Windows systems. This is as surprising as it sounds.”
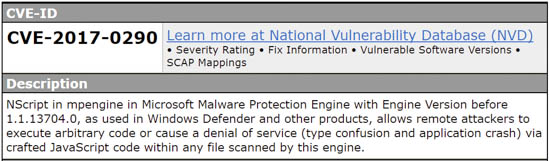
Source: Common Vulnerabilities and Exposures
Experts warn Project Zero’s exploit description may contain “useful” information
“Anti-virus [software] normally tries to intercept these things before you get to them,” said cyber security expert Graham Cluley.” He added that it was of “tremendous” importance that Microsoft release the patch so quickly, though he warned that Project Zero’s description of the vulnerability may contain information that malicious hackers might have found useful. “They can help the bad guys,” he added.
According to Microsoft’s security advisory published Monday, the full list of affected consumer and enterprise products includes Windows Defender (Windows 7 and later), Microsoft Security Essentials, Microsoft Forefront Endpoint Protection 2010, Microsoft Endpoint Protection, Microsoft Forefront Security for SharePoint Service Pack 3, Microsoft System Center Endpoint Protection and Windows Intune Endpoint Protection.
End users can check Windows Defender “About” page for version details
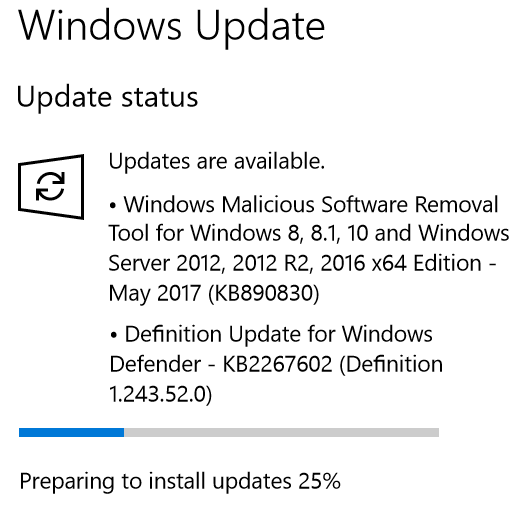
For end users, the easiest way to ensure the update has been applied is to open Windows Update and check if Definition Update for Windows Defender v.1.243.52.0 (KB2267602) or later is installed, along with Windows Malicious Software Removal Tool for May 2017 (KB890830). Alternatively, users can check that the Microsoft Malware Protection Engine version in their products is version 1.1.10701.0 or later. On Windows 7 through 10, this can be done by opening Windows Defender or Windows Defender Security Center from the Start Menu, clicking the “Settings” (wrench) icon and clicking “About.”




