A search warrant uncovered by Forbes shows how the iPhone maker intercepts and checks messages when illegal material—namely, evidence of child sexual abuse—is found within.
Apple isn’t manually checking all of your emails. It uses what most other major tech companies like Facebook or Google use to detect child abuse imagery: hashes.
When Apple systems see one of those hashes passing through the company’s servers, a flag will pop up. The email or file containing the potentially illegal images will be quarantined for further inspection.
Once the threshold has been met, that’s enough for a tech company to contact the relevant authority, typically the National Centre for Missing and Exploited Children [NCMEC]. NCMEC is a nonprofit that acts as the nation’s law enforcement clearinghouse for information regarding online child sexual exploitation. It will typically call law enforcement after being tipped about illegal content, often launching criminal investigations.
At this point, an Apple staff member then looks at the content of the files and analyses the emails.
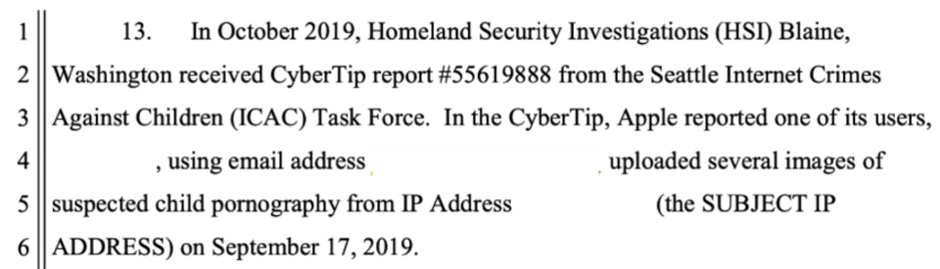
The search warrant showed an Apple employee’s comments on how they first detected “several images of suspected child pornography” being uploaded by an iCloud user and then looked at their emails. As no charges have been filed against that user, Forbes has chosen to publish neither his name nor the warrant.
“When we intercept the email with suspected images, they do not go to the intended recipient. This individual . . . sent eight emails that we intercepted. [Seven] of those emails contained 12 images. All seven emails and images were the same, as was the recipient email address. The other email contained 4 images which were different than the 12 previously mentioned. The intended recipient was the same”, the Apple workers’ comments read.
“I suspect what happened was he was sending these images to himself and when they didn’t deliver, he sent them again repeatedly. Either that or he got word from the recipient that they did not get delivered.”
The Apple employee then examined each of these images of suspected child pornography, according to the special agent at the Homeland Security Investigations unit.
So, in other words, Apple provided data on the iCloud user, including his name, address and mobile phone number that the user submitted when he signed up. The government also asked for the contents of the user’s emails, texts, instant messages and “all files and other records stored on iCloud”. A document outlining what further information was retrieved from Apple simply reveals a file on the iCloud account that was sent in early February without revealing what specific data was provided.
To be fair, Apple is in a "damned if they do, damned if they don't" position here – no one wants paedophiles to get away with anything. However, all this flies in the face of Apple's public stance which makes it appear hypocritical.




