On Sunday, Indian security researcher Hemanth Joseph claimed that he was successfully able to bypass the locked iPad he bought on eBay after entering very long strings of characters on the Wi-Fi Network setup page. The bug was discovered on iOS 10.1, which was released on October 24th.
When a user is met with an activation lock screen, one of the few functions still allowed is the ability to connect to a local Wi-Fi network. Though the researcher attempted to crash the internal lock screen service by entering long strings of characters in the WPA2-Enterprise credentials, he found that the screen would freeze after a while and prevent any further input. One work around was to use an iPad Smart Cover to put the device to sleep and then reopen it to restore the Wi-Fi setup menu.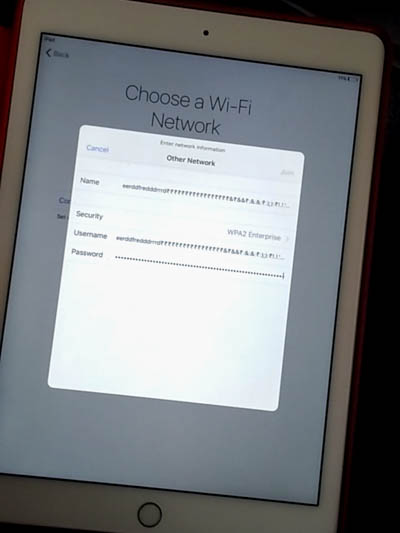
Source: Hemanth Joseph
"After 20-25 seconds the Add Wi-Fi Connection screen crashed to the iPad home screen, thereby bypassing the so-called Find My iPhone Activation Lock," he said in a blog post. “A character limit is important for fixing this bug.”
On Thursday, German security researcher Benjamin Kunz Mejri from Vulnerability Lab discovered the same exploit using the newer iOS 10.1.1, which was released on November 5th.
The bug was reproduced by overflowing the Wi-Fi form fields with long strings of characters, after which a Smart Cover was used to unfreeze the device. However, this researcher’s method required rotating the tablet’s screen in order to crash the software to the Home screen.
Apple told the Indian researcher on November 5th in an email that it will prepare a security update for customers, while urging him not to disclose any information until the investigation was complete.
Another related exploit was recently discovered allowing an attacker to access photos and contacts from a locked iOS device, according to two sources who posted videos of the procedure. The exploit involves using the VoiceOver accessibility feature when Siri is enabled to bypass a device’s passcode. Unlike the activation lock method, this issue affects iOS versions 8, 9 and 10 including the most recent iOS 10.2 beta 3.
The company has yet to return a request for comment on the wider exploit but is probably investigating both bugs and will tell us more on its security updates page soon.




